Protecting your cryptocurrency from hacks is more critical than ever. As crypto scams and hacks evolve, users must use strong security to protect their assets. This article gives crypto holders strategies to protect their investments. It suggests using secure digital wallets, enabling two-factor authentication, and recognizing phishing threats. Updating security software and checking transaction details are vital. They can significantly lower the risk of hacks.
Choosing the Right Wallet for Maximum Security
A good crypto wallet can reduce hack risks and protect your assets. This section will help you understand cold, hot, and multi-signature wallets. It will also help you choose the right one for your needs.
Offline Storage (Cold Wallets) for Long-Term Security
Cold wallets are best for storing crypto offline. They are less vulnerable to online threats. Below is a comparison of the advantages and risks of using cold wallets:
| Advantages | Risks |
|---|---|
| Higher security since they are offline, reducing hacking risk | Less convenient for daily transactions |
| Ideal for long-term storage of large amounts of crypto | Can be lost if not properly stored (e.g., hardware) |
| Private keys are never exposed to the internet | More expensive than hot wallets |
| Suitable for long-term investors | Transactions are slower due to offline access |
Online Wallets (Hot Wallets) for Everyday Use
Hot wallets are connected to the internet and offer convenience for frequent transactions. However, they come with increased risks. Here’s a breakdown of their pros and cons:
| Advantages | Risks |
|---|---|
| Convenient for frequent transactions | More vulnerable to hacking due to constant online access |
| Accessible from any internet-connected device | Not ideal for storing large amounts of cryptocurrency |
| Typically free or low-cost | Requires strong security measures (e.g., 2FA) |
| Suitable for everyday spending and small holdings | Susceptible to malware or phishing attacks |
Multi-Signature Wallets for Enhanced Protection
Multi-signature wallets provide enhanced security by requiring multiple approvals for transactions. Here’s how they compare:
| Advantages | Risks |
|---|---|
| Multiple keys reduce the risk of unauthorized access | More complex setup and use |
| Ideal for shared or organizational accounts | Can be slower, as all keyholders need to approve a transaction |
| Adds an extra layer of security beyond a single key | Requires coordination among multiple parties |
Strengthening Passwords and Enabling Two-Factor Authentication
To secure your cryptocurrency, start with two things. First, create a strong password. Second, enable two-factor authentication (2FA). These steps are vital. They block unauthorized access and hacking. They greatly boost your protection.
Creating and Managing Strong Passwords
Creating a strong, unique password is the cornerstone of cryptocurrency security. To protect your crypto assets, use long, complex passwords. They should combine uppercase and lowercase letters, numbers, and special characters. Passwords must be at least 16 characters long. This will resist common hacking techniques, like brute force attacks.
It is best to use a password manager for managing passwords across platforms. Password managers create and securely store random, complex passwords. They free you from remembering multiple, tough passwords. Services like LastPass and Bitwarden are popular choices for password management. Additionally, passwords should be changed regularly to prevent unauthorized access.
Steps for Managing Strong Passwords:
- Generate a complex password with a mix of letters, numbers, and symbols.
- Use a password manager to securely store and auto-fill your passwords.
- Regularly update passwords, especially for critical accounts like cryptocurrency exchanges and wallets.
- Avoid reusing passwords across different platforms to minimize exposure from potential breaches.
Setting Up Two-Factor Authentication (2FA)
Enabling two-factor authentication (2FA) is a simple but effective way to secure your crypto accounts. 2FA requires a second form of identification, such as a code generated by an authentication app, in addition to your password. This added security means that, even with your password, a second factor is needed to log in.
To set up 2FA, start by downloading an authenticator app such as Google Authenticator or Authy. These apps generate time-based, one-time codes that refresh every 30 seconds. Follow these steps to activate 2FA on your crypto accounts:
- Download Authenticator App: Install the Crypto.com Authenticator app on your device from the app store.
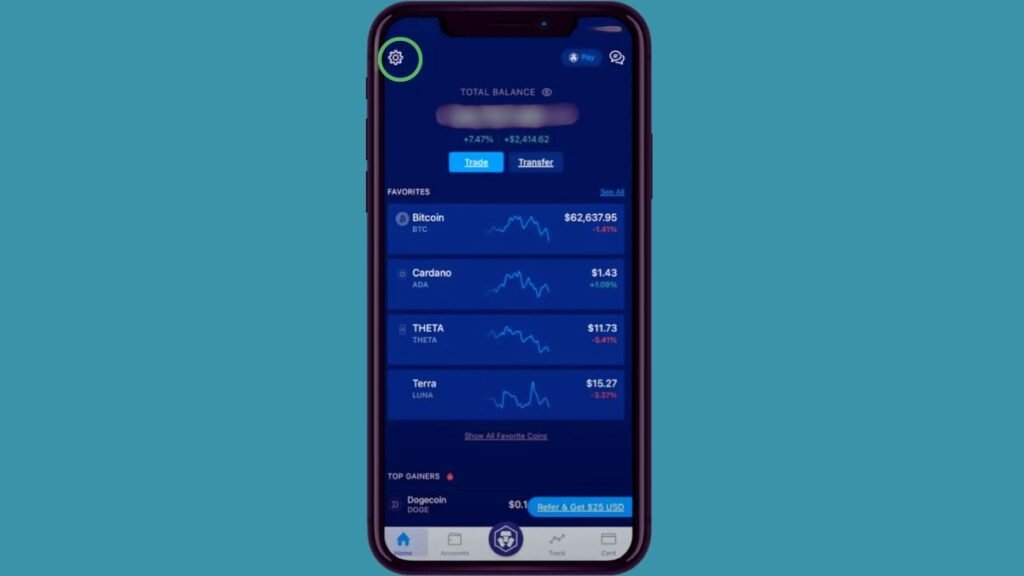
- Access 2FA Settings: Open the Crypto.com app, tap on the Settings icon in the top left corner, and select the “2-Factor Authentication” option.
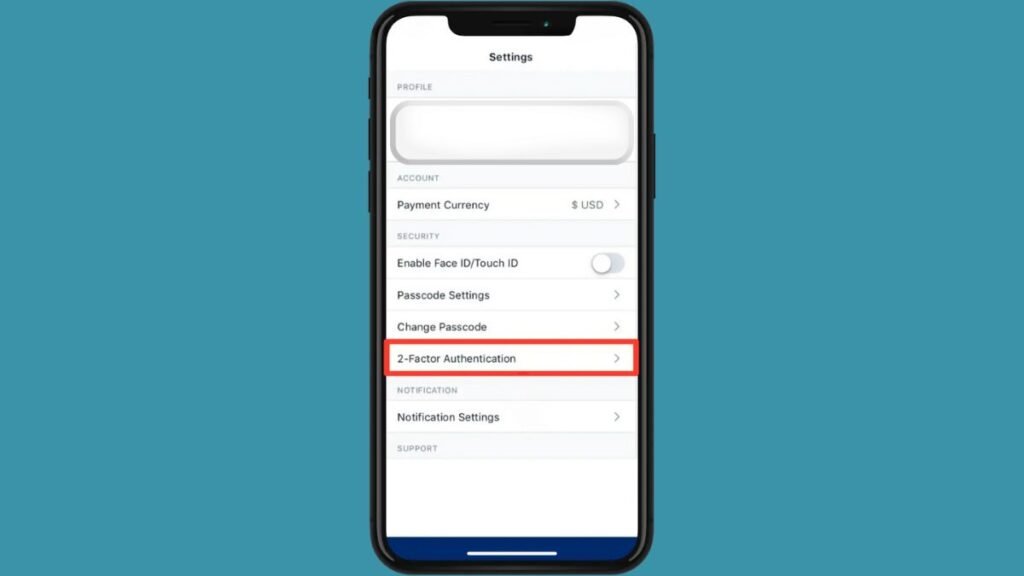
- Enable 2FA: On the 2FA screen, toggle the “Enable 2FA” option to turn it on.
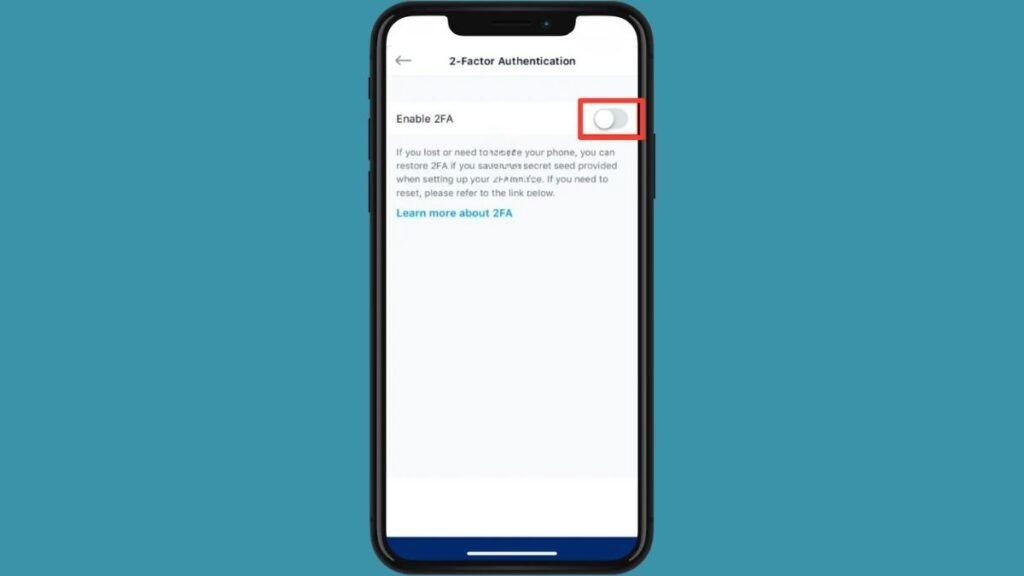
- Save QR Code: A pop-up will appear with a QR code. Take a screenshot of the QR code and save it to your device, but do not scan the demo image provided.
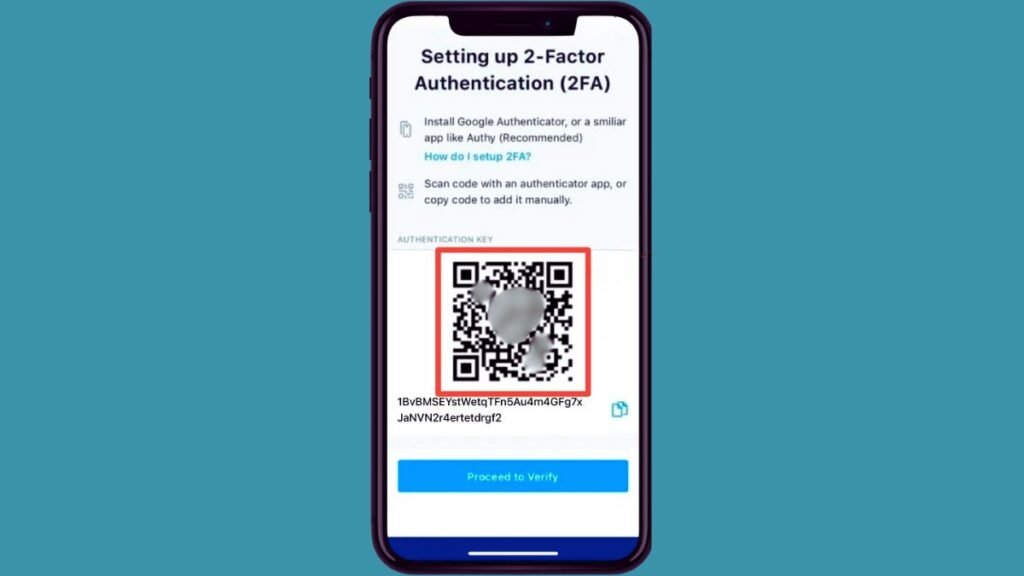
This process greatly cuts your risk of hacking, especially from phishing attacks that steal passwords.
Biometric Authentication for Extra Security
For better security, many wallets and exchanges now use biometrics. This includes fingerprint and facial recognition. It adds security beyond passwords and 2FA. It uses your unique physical traits, which are hard to replicate.
Setting up biometric authentication is typically quick and easy. On most devices, you can activate biometrics through the security settings of your wallet or exchange app. The following steps outline the process on Binance:
- Log in to your Binance account: Open the Binance app on your mobile device and log in.
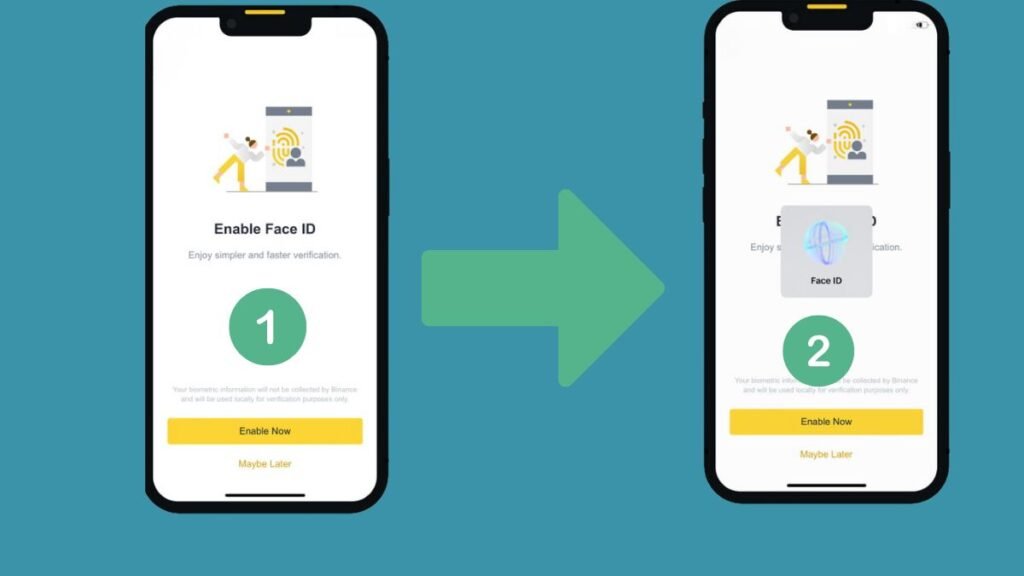
- Enable Biometric Authentication: After logging in, you must activate it. Tap [Enable Now].
- Verify Using Biometrics: From now on, you will be able to log in using biometric authentication, such as facial recognition.
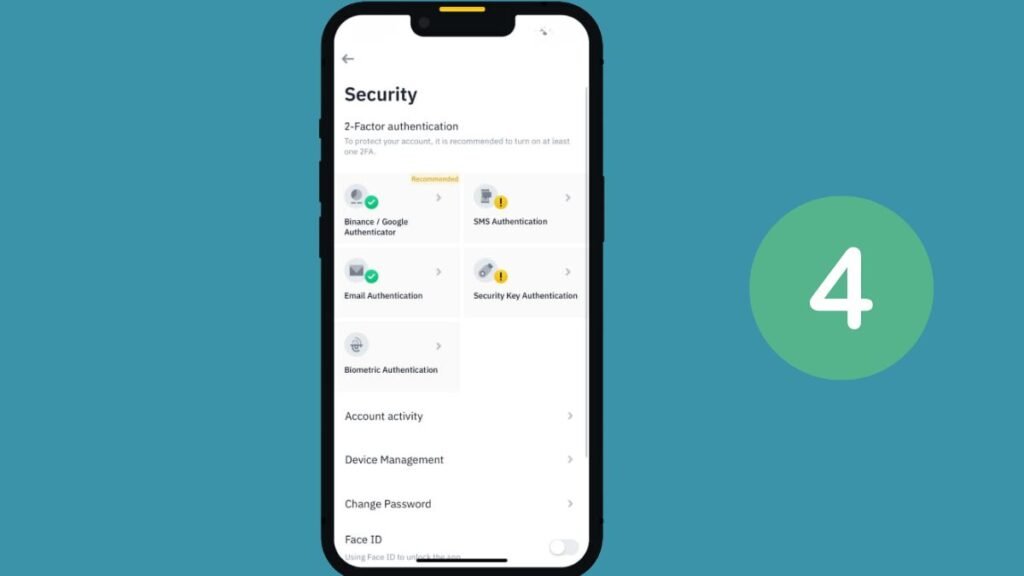
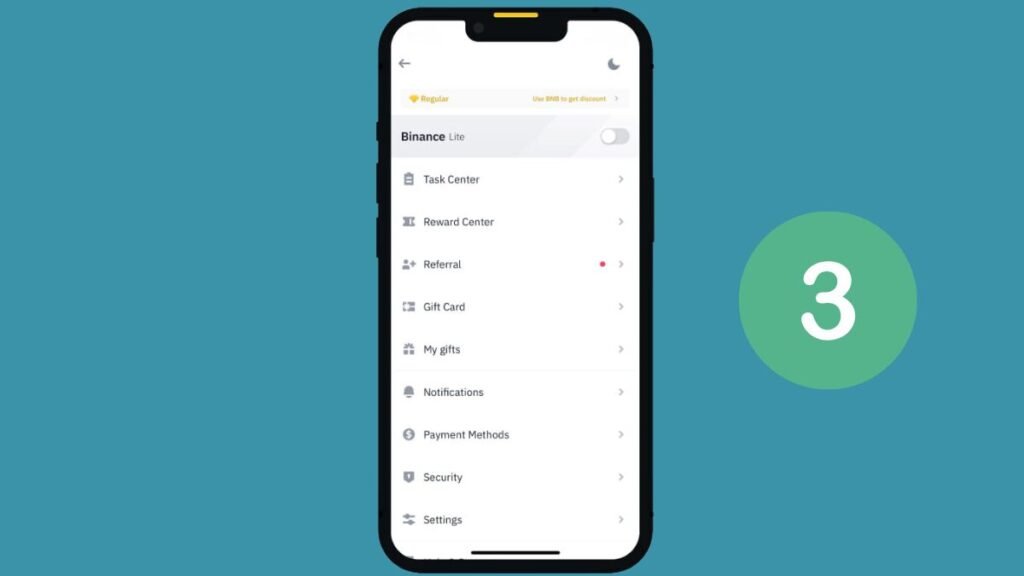
- Alternative Method: To enable Biometric Authentication, visit your profile page. Select Security. Then tap Biometric Authentication and choose Add Biometric Authentication.
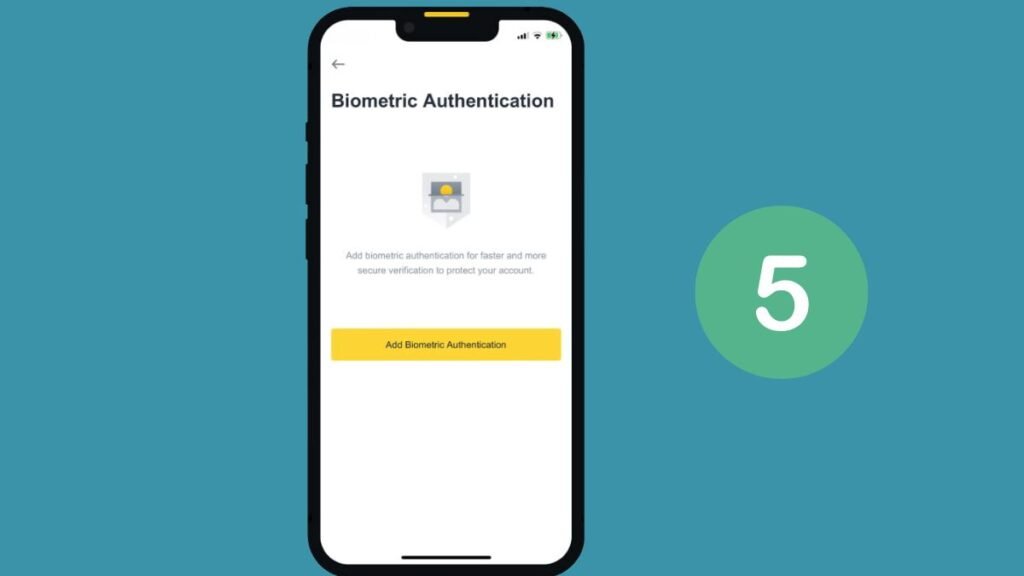
Biometric authentication is great for mobile users. It lets them quickly and securely access their accounts, without passwords or 2FA codes. However, always ensure you have backup authentication methods in place in case of device failure.
Identifying and Preventing Phishing Attacks
Phishing attacks are a top method for stealing cryptocurrency. Hackers use them often. These attacks trick users into revealing sensitive information. They impersonate legitimate services to do this. In 2024, spotting these scams is vital to avoid big losses.
Recognizing Phishing Emails and Websites
Phishing emails and fake websites often mimic real crypto platforms. These include exchanges and wallets. The goal is to lure users into providing sensitive information under false pretenses. These scams may urge users to verify their identity. They may claim an urgent issue with their account or offer enticing rewards. However, the scammer can drain the user’s crypto accounts once the user gives the info.
Here are key tips to recognize phishing attempts:
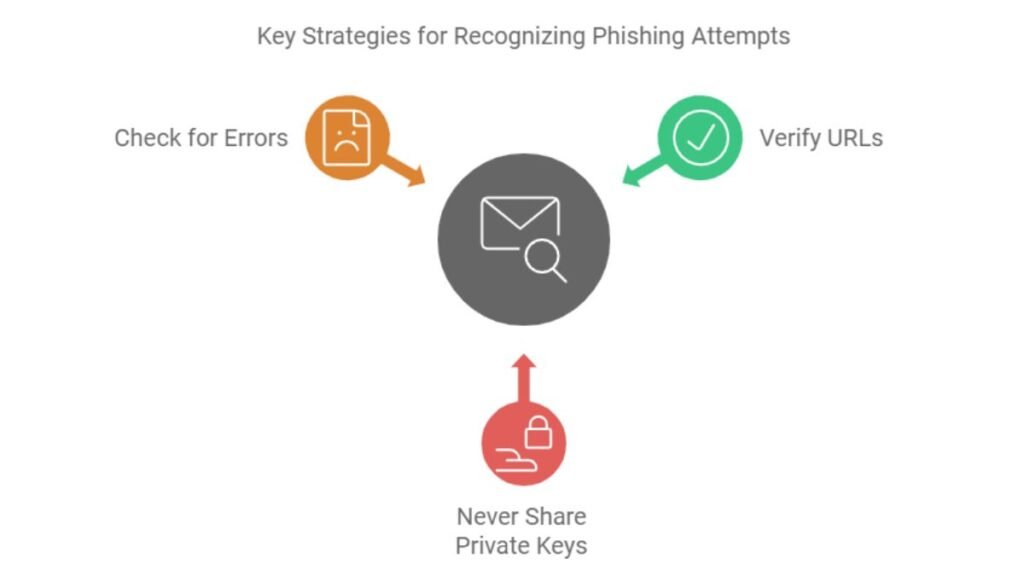
- Always verify URLs: Look for small spelling mistakes or extra characters in web addresses that mimic real sites.
- Never share your private keys: Legitimate services will never ask for private keys or passwords via email or messages.
- Check for errors: Phishing emails often contain grammar mistakes or awkward phrasing. Legitimate companies typically ensure their communications are error-free.
Avoiding Address Poisoning Scams
Address poisoning scams are another method hackers use to trick users. They aim to get users to send cryptocurrency to fake addresses. In this scam, attackers change transaction details. It seems you’re sending funds to the correct address. But, they have altered it.
To avoid falling victim to these scams:
- Double-check all transaction details: Always confirm the recipient’s wallet address before a transaction. Do this manually. Don’t rely solely on autofill or copy-paste functions.
- Use transaction verification tools: They check wallet addresses before processing payments. This helps ensure the address is legitimate.
Keeping Software and Devices Updated
It’s vital to keep your software and devices up to date. This protects your cryptocurrency. Cyberattacks often target outdated systems, exploiting known vulnerabilities. Regularly updating your OS, apps, and wallets helps protect against threats. It patches security gaps that hackers may exploit.
Updating Wallet Software Regularly
Cryptocurrency wallets often update to fix security flaws or improve features. Not updating your wallet software risks your assets. Attackers can exploit older versions. Popular wallets like Exodus and MetaMask offer updates every few weeks. They often include critical security patches. To ensure you’re protected:
- Check for updates frequently in the app store or wallet’s website.
- Turn on automatic updates when possible to avoid missing important patches.
- Only use official sources to download wallet software updates.
Device Operating System and Application Updates
Besides your wallet, update your device’s OS and crypto apps. Hackers often exploit flaws in outdated operating systems, especially on jailbroken or rooted devices. Major operating systems, like iOS and Windows, regularly push updates to fix these vulnerabilities. Here’s how you can secure your devices:
- Enable automatic updates for your operating system.
- Avoid pirated software and suspicious websites. They can introduce malware to your system.
- Consider using antivirus software and firewalls. They add extra protection.
Note
Updating your devices reduces exposure to malware. It also lowers the risk of losing your crypto to cyberattacks.
Using VPNs and Secure Networks for Transactions
Using unsecured networks for cryptocurrency transactions can be risky. Hackers may intercept your data. A VPN or a secure, trusted network is one of the best ways to protect your data and assets during transactions. A VPN adds layers of encryption and security. It keeps sensitive data, like private keys and transaction details, safe from cybercriminals.
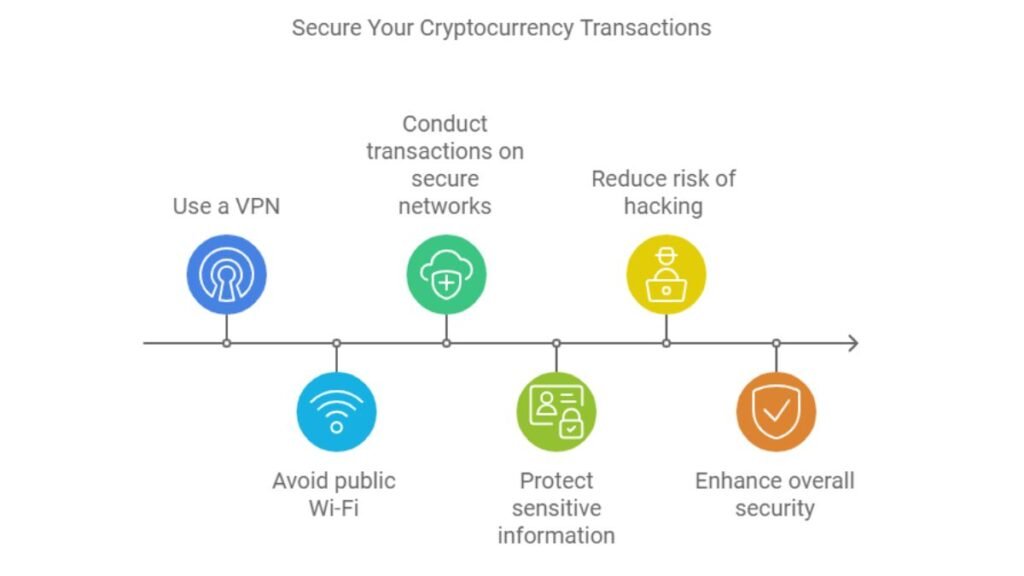
Benefits of Using a VPN for Crypto Transactions
A VPN protects your identity and finances. It does this by masking your IP address and encrypting all internet data. This makes it harder for hackers, governments, and others to trace your actions or steal your data in cryptocurrency transactions. Popular VPNs like NordVPN and ExpressVPN offer military-grade encryption (AES-256). They have privacy features, like a kill switch. It cuts off your internet if the VPN connection drops, ensuring your true IP address is never exposed.
A VPN for crypto trading hides your data with encryption. This is vital when accessing exchanges or wallets. It keeps your info safe from prying eyes. This is vital when trading across different exchanges or countries with strict geo-restrictions. Also, many VPNs have added security. They include malware blocking and ad protection. These features help prevent phishing attempts.
Avoiding Public Wi-Fi for Crypto Transactions
Public Wi-Fi networks, such as those found in cafes or airports, are notoriously insecure. Hackers often exploit these networks. They can intercept sensitive cryptocurrency data being transmitted. So, it is critical to avoid any cryptocurrency transactions on public Wi-Fi. Even if you use a VPN, public Wi-Fi can introduce vulnerabilities. Instead, it’s safer to connect through your home network or use a trusted mobile hotspot.
If you must use public Wi-Fi, always use a VPN. It adds security. Also, check that the website has HTTPS encryption. Look for a padlock symbol next to the URL. This ensures that your data is transmitted securely.
Explore More:
- Cold wallets for long-term crypto storage
- Using two-factor authentication (2FA)
- How to identify dusting attacks on explorers
- Using cryptocurrencies securely
- Token burning mechanisms
Secure your cryptocurrency. Protect your assets from rising hacks, phishing, and other threats. You can significantly enhance your security by following best practices. They include choosing the right wallet, using strong passwords, enabling two-factor authentication, and avoiding phishing scams. Also, keep software and devices updated. Use trusted networks or VPNs for transactions. They add important security.



















