Cryptocurrency wallets are vital in digital finance. They let users store, manage, and access their assets with security measures in place. Hot and cold wallets are key to managing crypto. Each type has its own benefits and risks. Knowing these differences is key for choosing a wallet. This is true for both newcomers and experienced traders. This guide will explain the key differences between hot and cold wallets. It will focus on wallet security and accessibility. This will help you choose the best option for your needs.
Understanding Hot Wallets
Hot wallets are essential in crypto. They give users fast, easy access to their digital assets. These wallets are always online. They are ideal for daily transactions and frequent trades. However, their online nature exposes them to security risks, like hacking or malware. This makes them a more vulnerable option than cold wallets.
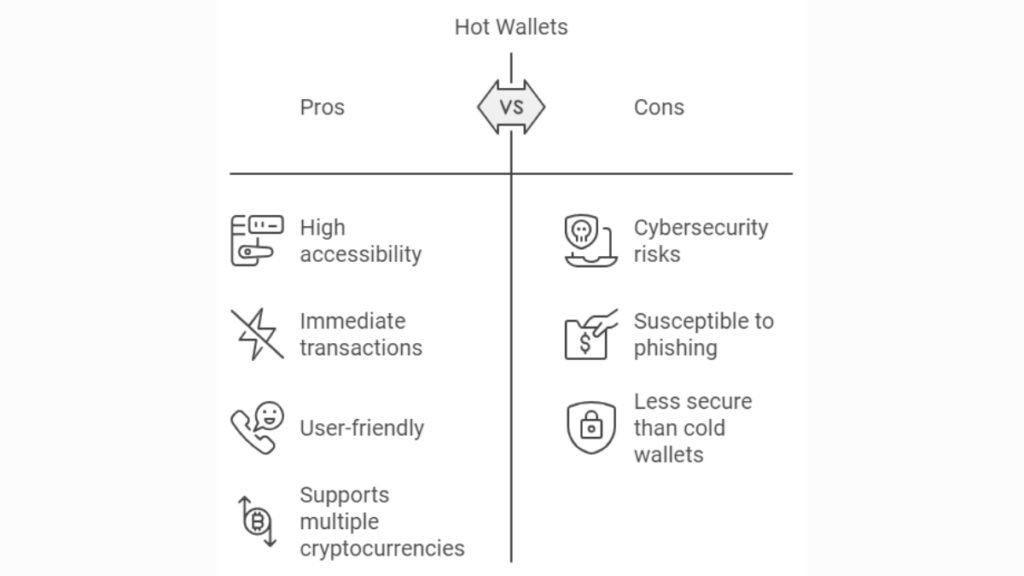
What Are Hot Wallets?
Hot wallets are digital tools that allow users to store, send, and receive cryptocurrencies by maintaining a constant connection to the internet. Because of this, they are highly accessible, providing users with immediate access to their crypto holdings. This makes hot wallets a preferred choice for traders and users who frequently engage in transactions. However, this convenience comes at a cost—since they are always online, they are more susceptible to cyber threats like hacking and phishing attacks.
Some well-known hot wallets include MetaMask, Trust Wallet, and Coinbase Wallet. These wallets often support multiple cryptocurrencies. So, they are great for users with diverse portfolios. However, 2FA and encryption have improved security. But, it’s no match for the offline security of cold wallets.
Types of Hot Wallets
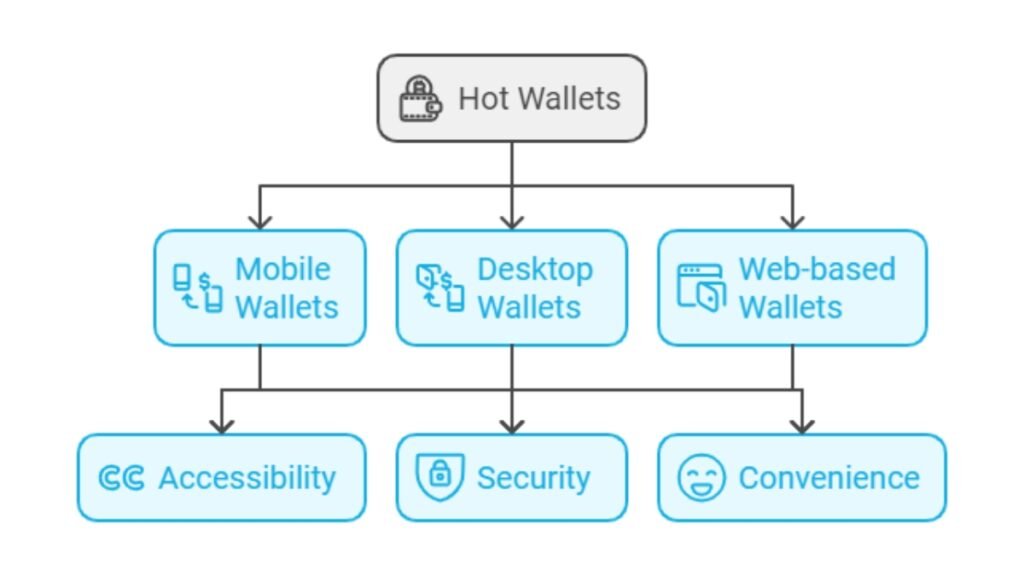
Hot wallets come in several forms, each suited to different user preferences and needs. These include mobile wallets, desktop wallets, and web-based wallets, all of which offer varying levels of accessibility, security, and convenience.
| Type | Accessibility | Security | Ease of Use |
|---|---|---|---|
| Mobile Wallets | Accessible from smartphones | Medium security; susceptible to hacks | Highly convenient for on-the-go transactions |
| Desktop Wallets | Accessed via installed software on PC | Higher security than mobile/web wallets but still online | Suitable for users comfortable with desktop interfaces |
| Web-Based Wallets | Access through browsers | Lowest security; vulnerable to phishing or malware | Easy to use, no installation required |
- Mobile Wallets: These wallets, such as Trust Wallet or Coinbase Wallet, allow users to manage their crypto directly from their phones. This offers the convenience of accessing funds on the go, but the mobile devices’ constant internet connection increases the risk of theft.
- Desktop wallets are more secure than mobile wallets, but they are still at risk from online threats. Examples include Electrum and Mycelium. They are more robust, but they are still online, so they are less secure than offline options.
- Web-Based Wallets: Web wallets run on browser extensions or websites. They are the least secure. They are, but, the easiest to access. Examples include MetaMask, which integrates with dApps.
Benefits and Risks of Hot Wallets
Hot wallets are great for users who need to access their crypto often or make frequent transactions. Hot wallets are always connected. So, they allow immediate transactions. This is crucial for traders and dApp users. However, this convenience comes with increased security risks.
| Benefit | Risk |
|---|---|
| Hot wallets provide users with instant access to their crypto, allowing for quick transactions and trading. | Being online exposes hot wallets to potential attacks. Hackers may gain access through malware, phishing, or exploiting vulnerabilities. |
| Most hot wallets come with simple, intuitive interfaces, making them easy to use even for beginners. | If a hacker gains access to a hot wallet, there is no way to reverse transactions or recover stolen funds. |
Note
For these reasons, hot wallets are vital for frequent crypto transactions. But, users should keep only a small amount of crypto in them for daily use. They should store the rest in a more secure, offline cold wallet.
What Are Cold Wallets?
Cold wallets are secure cryptocurrency storage solutions. They suit users who prefer security over convenience. Unlike hot wallets, which are always online, cold wallets store private keys offline. They offer strong protection against cyberattacks. This makes them a preferred choice for long-term investors who don’t need frequent access to their funds. Cold wallets are best for storing large amounts of crypto. They eliminate the risks of online storage.
Overview of Cold Wallets
Cold wallets are tools for storing crypto. They keep private keys offline, so they can’t be hacked. Since these wallets do not have an internet connection, they are impervious to phishing, malware, and other online threats. Their offline nature makes cold wallets very safe for storing cryptocurrency. They are best for long-term investors.
Types of Cold Wallets
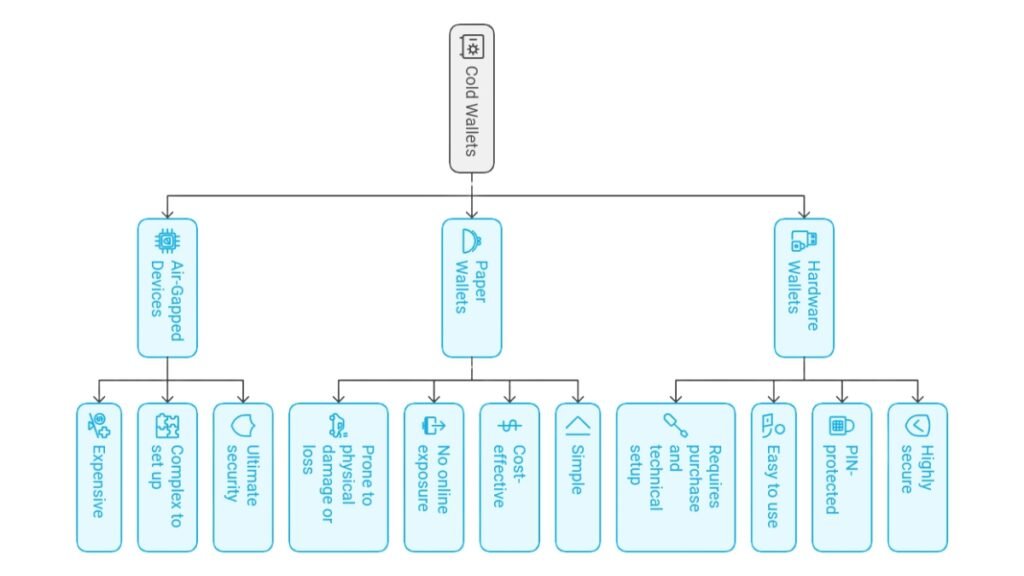
There are various types of cold wallets available, each offering unique features depending on user needs. Below is a breakdown of the most common types:
| Type | Description | Pros | Cons |
|---|---|---|---|
| Hardware Wallets | Devices like Ledger or Trezor that store private keys offline. | Highly secure, PIN-protected, easy to use. | Requires purchase and technical setup. |
| Paper Wallets | Printed documents containing private keys. | Simple, cost-effective, no online exposure. | Prone to physical damage or loss. |
| Air-Gapped Devices | Computers or devices that never connect to the internet. | Ultimate security for large holdings. | Complex to set up, expensive. |
- Hardware Wallets: They are the most popular cold wallets. They offer high security by storing private keys offline on devices. Devices like the Ledger Nano and Trezor are well-known for their ease of use and PIN-protected access, making them ideal for securing large sums of crypto.
- Paper Wallets: A paper wallet involves printing out the private and public keys on paper. While this method is offline and cannot be hacked, it is vulnerable to physical damage or loss if not stored securely.
- Air-Gapped Devices: These devices never connect to the internet. They are the most secure for crypto storage. They are used primarily by those seeking to secure significant cryptocurrency holdings but require advanced technical knowledge.
Long-Term Storage and Security Benefits
Cold wallets are the preferred choice for long-term storage because they offer unmatched security. Since they are offline, cold wallets are protected from online threats like hacking, phishing, and malware. They are highly recommended for users who will hold a lot of cryptocurrency for a long time without frequent transactions.
The high security has trade-offs in convenience. Accessing funds in a cold wallet requires connecting the device to an online system. However, for long-term holders, this extra step is a small price to pay for the enhanced security.
Comparing Hot and Cold Wallets
When choosing between a hot and cold wallet, know their key differences in functionality, security, and accessibility. Hot wallets are best for users who need quick access to their crypto for daily transactions. Cold wallets are better for long-term storage and security.
Security Considerations
Security is the most significant distinction between hot and cold wallets. Cold wallets are offline. They offer superior protection as they aren’t internet-connected. This eliminates the risk of hacks, phishing attacks, and malware, making them the safest option for holding large amounts of cryptocurrency for extended periods. Popular cold wallets, like Ledger and Trezor, store private keys offline. They are PIN-protected, adding extra security.
Hot wallets are always online, which makes them vulnerable to cyber threats. Many hot wallets use encryption, 2FA, and recovery seeds to protect private keys. But, they can’t match the security of cold wallets. As a result, hot wallets are more susceptible to hacking, particularly when used on compromised devices.
Accessibility and Convenience
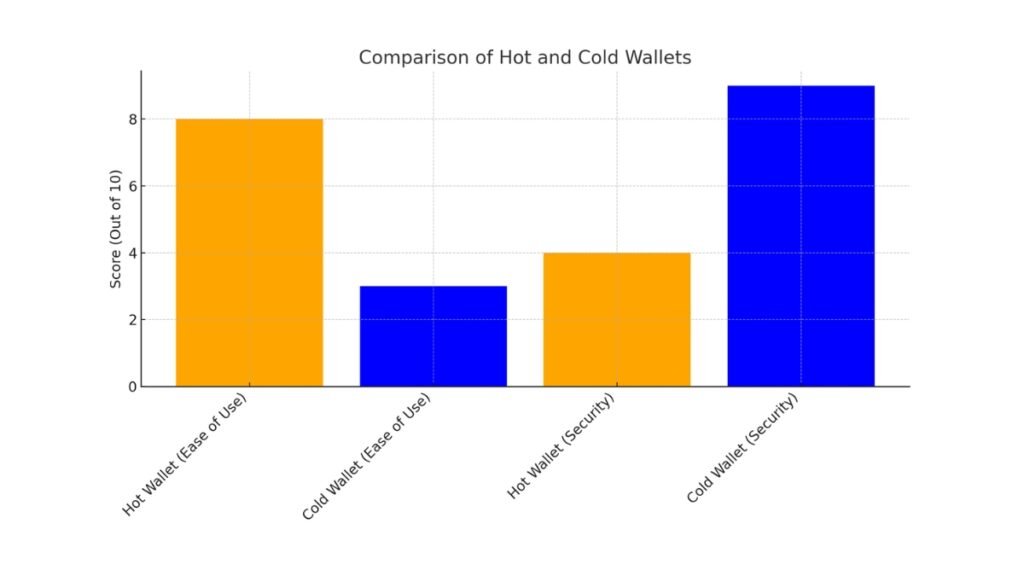
Here is a bar chart that compares hot and cold wallets based on ease of use and security, following the information provided in the paragraph. The hot wallet excels in ease of use, while the cold wallet is superior in security.
In terms of ease of use, hot wallets stand out. They offer quick, easy access to funds. So, they are ideal for frequent transactions and using dApps. Hot wallets like MetaMask, Trust Wallet, and Coinbase Wallet work on smartphones, tablets, and desktops. They let you quickly access your crypto assets.
Cold wallets are less convenient because they operate offline. To transfer funds, users must connect their cold wallet to an online device. This is more time-consuming. Cold wallets are better for users who rank security over convenience. They are a good option for those who don’t need regular access to their funds.
| Use a Hot Wallet if | Use a Cold Wallet if |
|---|---|
| You need to make frequent transactions. | You plan to store crypto for the long term. |
| You interact with dApps or decentralized exchanges (DEXs). | Security is your top priority. |
| You want immediate access to your funds. | You hold large amounts of cryptocurrency. |
Choosing the Right Wallet for Your Needs
Choosing the best crypto wallet depends on your needs. Do you value convenience for trading, or security for long-term storage? Hot wallets and cold wallets serve different purposes. Your choice should reflect how often you access your crypto and how much security you need.
Factors to Consider in Wallet Selection
When deciding between hot and cold wallets, consider factors like:
- Frequency of Transactions: A hot wallet is better for frequent trading. It is always online and easy to use. These wallets, like MetaMask or Trust Wallet, provide real-time access to your funds, making them ideal for daily activities.
- Cryptocurrency Stored: For users with a lot of crypto, a cold wallet is better. Cold wallets, such as Ledger or Trezor, store your private keys offline, protecting them from online threats like hacking and phishing. If security is your priority, use cold wallets. They keep your keys safe from online threats.
- Technical Expertise: Hot wallets are generally more user-friendly and require less technical knowledge, making them a good choice for beginners. Cold wallets may need more setup and maintenance. But, they offer better security for users with higher technical skills.
Best Practices for Secure Wallet Usage
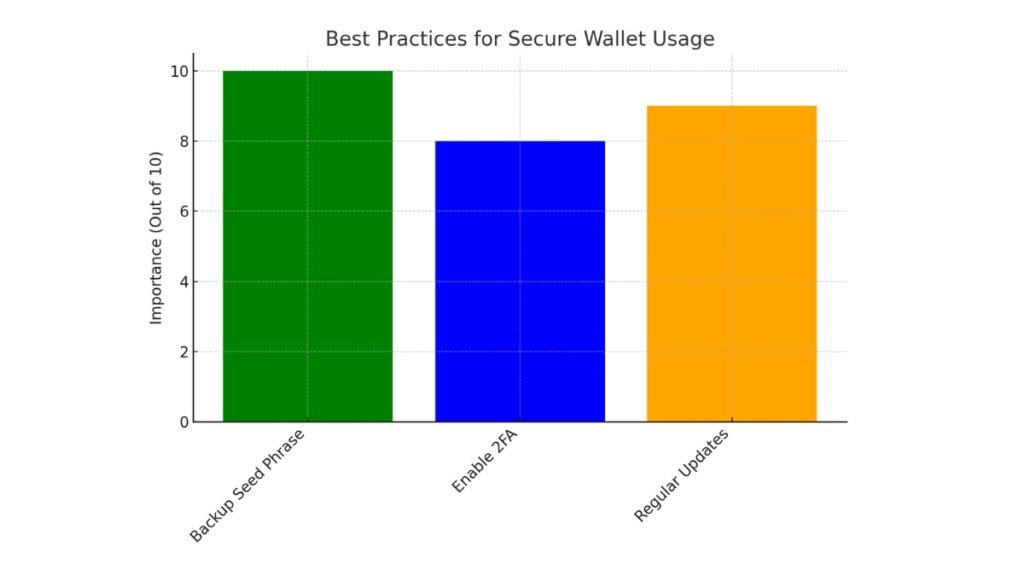
The bar chart shows the importance of secure wallet usage best practices, based on the previous paragraph. The chart scores the following practices:
- Backup Seed Phrase: Rated as the most important (10/10).
- Enable Two-Factor Authentication (2FA): Rated 8/10 for adding an extra security layer.
- Regular Software Updates: Rated 9/10 for ensuring protection against vulnerabilities.
No matter which wallet you choose, security is key. Follow best practices to protect your crypto:
- Backup Your Seed Phrase: Ensure you back up your wallet’s recovery seed phrase and store it in multiple secure locations. Losing this phrase can mean losing access to your funds permanently. Consider using secure physical storage solutions like metal backups or encrypted storage.
- Enable Two-Factor Authentication (2FA): For hot wallets, enabling 2FA adds an additional layer of security, making it harder for unauthorized users to access your wallet. Many wallets, including exchanges, offer this feature to strengthen account protection.
- Update Wallet Software Regularly: Always update your wallet and related software to fix vulnerabilities. Wallet providers often release patches for security flaws. It’s vital to apply these updates promptly to keep a secure environment.
You Might Also Like:
- Cold storage vs hot wallets
- What is a hardware wallet
- Benefits of cold storage
- Public and Private Keys
- Choosing a Crypto Exchange
Choosing between hot and cold wallets comes down to your specific needs. If convenience for daily transactions is essential, a hot wallet is your best option. If long-term security and protection from online threats are your priorities, a cold wallet is the way to go. To keep your assets safe, follow best practices. Back up your seed phrases and enable two-factor authentication.



















