Cryptocurrency security is essential for newcomers to digital assets. With the rise in cyberattacks, it’s vital to protect your investments. This guide will cover the basics to keep your crypto safe. It will include two-factor authentication and secure passwords. Following these security best practices can help beginners. It can protect their digital assets from phishing and hacking.
Securing Your Cryptocurrency Wallets
Protecting your cryptocurrency wallet is crucial. It safeguards your digital assets. Use a hardware (cold) wallet or a software (hot) wallet. Either way, secure your private keys. Wallets store these private keys, which grant access to your cryptocurrency. Let’s explore the key differences between hardware and software wallets. We’ll also cover best practices, like using strong passwords and two-factor authentication (2FA).
Types of Cryptocurrency Wallets
When it comes to securing your crypto, choosing the right type of wallet is vital. Hot wallets, or software wallets, are connected to the internet. They’re convenient for frequent transactions. These wallets are often accessible on mobile apps or desktop software. But, this convenience raises the risk of hacks and cyberattacks. Their constant online presence makes them more vulnerable. Cold wallets, , store private keys offline, offering enhanced security. Hardware wallets like Ledger or Trezor are popular choices, especially for long-term storage. Cold wallets aren’t online. They’re nearly immune to hacking. But they’re less convenient for regular transactions.
Using Strong Passwords and Password Managers
Creating a strong and unique password for your crypto wallet is critical. A weak password is like leaving the door to your digital assets wide open. Passwords should be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and symbols. To track these passwords, use a password manager. It securely stores and encrypts them. This prevents you from reusing the same password across platforms.
A password manager is a vault for your keys. Just as you wouldn’t use the same key for your home, car, and safe, use different, strong passwords for every account. This ensures that even if one password is compromised, your other accounts remain secure.
- Create a password with at least 12 characters.
- Include numbers, symbols, and uppercase/lowercase letters.
- Avoid using the same password across multiple platforms.
- Use a trusted password manager to store your passwords securely.
Authentication (2FA)
Two-factor authentication (2FA) is a top way to secure your crypto accounts. It adds protection beyond just a password. This method requires two verifications. Typically, it’s: 1. Something you know (your password). 2FA adds a second login step. Even if someone gets your password, they would still need the second factor. This greatly reduces the risk of unauthorized access.
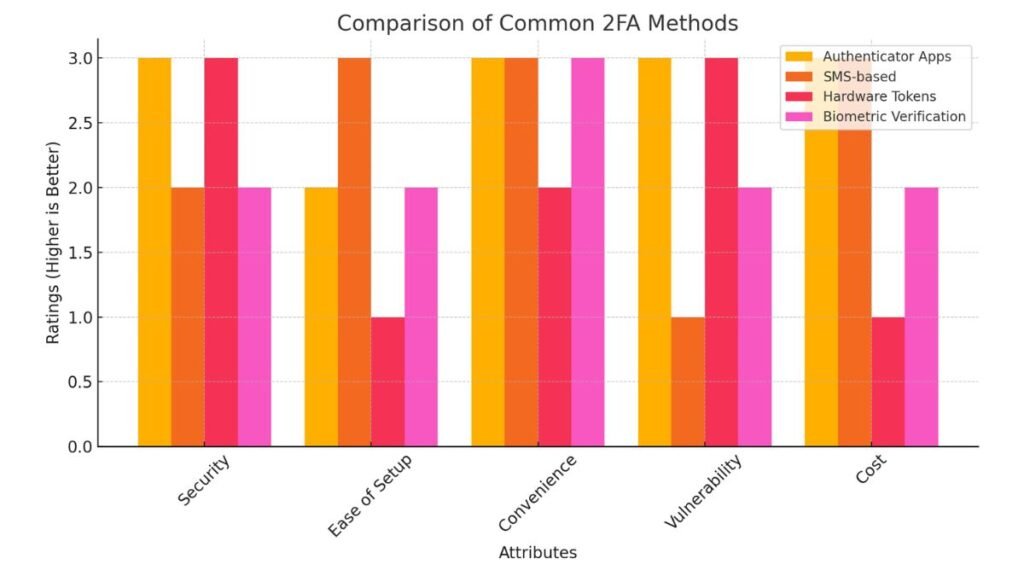
Authenticator apps, such as Google Authenticator or Authy, are the most secure and convenient options for 2FA. These apps generate a code that refreshes every 30 seconds, making it nearly impossible for hackers to use stolen information. In contrast, SMS-based 2FA, while still helpful, is more vulnerable to attacks such as SIM-swapping, where hackers redirect your mobile service to their device.
| 2FA Method | Description | Pros | Cons |
|---|---|---|---|
| Authenticator Apps | Time-sensitive codes generated on apps like Google Authenticator or Authy. | Secure, works offline, refreshes every 30 seconds | Requires access to the phone or device where the app is installed |
| SMS-based | One-time passcode sent via text message to your registered phone number. | Easy to set up, widely available | Vulnerable to SIM-swapping, can be intercepted over networks |
| Hardware Tokens | Physical devices (e.g., YubiKey) that generate authentication codes or require physical interaction. | Extremely secure, cannot be intercepted remotely | Expensive, requires physical possession of the token |
| Biometric Verification | Uses fingerprint, face recognition, or other biometrics to authenticate users. | Convenient, personalized security | Limited to devices with biometric capabilities, hardware-dependent |
2FA may cause minor annoyances, like needing backup codes if you lose your 2FA device. But, its protection far outweighs these drawbacks. Without 2FA, if your password is compromised, you could lose your entire crypto investment. By enabling 2FA, you add an essential safeguard, giving you peace of mind and enhanced control over your digital assets.
Protecting Against Phishing and Scams
Phishing scams are one of the most common and dangerous methods hackers use to steal cryptocurrency. These scams can be fake emails, websites, or social media accounts. They pretend to be legitimate exchanges or wallets. Beginners must learn to spot and avoid these threats. It’s key to safeguarding their crypto investments.
Recognizing Common Phishing Tactics
Crypto phishing attacks often involve fake emails, websites, or messages. They look like they’re from trusted sources, such as Coinbase or MetaMask. These fraudulent messages ask users for sensitive info. This includes their private keys and login credentials. Once you submit this information, scammers can steal your assets.
Here are some common phishing tactics:
- Fake Exchange Emails: Scammers send emails that look identical to official ones from exchanges. They often contain urgent messages, like requests to verify your account or resolve security issues. Clicking on the included link usually leads to a fake login page designed to steal your credentials.
- Typosquatting: Scammers create websites with slightly altered URLs that resemble legitimate ones. For example, changing “coinbase.com” to “co1nbase.com” is a subtle yet dangerous trick.
- Airdrop Scams: Users are lured into fake airdrops. They must sign transactions or share their private keys. This can give scammers access to your wallet.
To Avoid Phishing Attacks:
- Always verify the URL begins with “HTTPS” and looks authentic.
- Never click on links in unsolicited emails.
- Use anti-phishing codes provided by exchanges like KuCoin to confirm legitimacy.
Avoiding Fake Crypto Wallets and Exchanges
Fake crypto wallets and exchanges mimic real ones to steal your keys or crypto. These scams often involve setting up websites that look almost identical to trusted services. Scammers can create fake apps or websites. These trick users into giving their private info.
Here’s how you can spot and avoid these fake platforms:
- Check Community Reviews: Before downloading a wallet or signing up for an exchange, read user reviews and check trusted forums. Legitimate platforms usually have a long history of user engagement and reviews.
- Verify SSL Certificates: Always ensure the website has a valid SSL certificate. Look for the padlock symbol in the address bar to confirm the site is secure.
- Use Trusted Sources: Download wallets only from official sites or app stores. Avoid third-party downloads; they could be compromised.

Here is a checklist visualization in the form of a horizontal bar chart. Each bar represents an important aspect to consider when evaluating a crypto wallet or exchange. The importance level is an arbitrary value that helps to visualize which steps are crucial to ensure safety.
Secure Storage Solutions for Long-Term Crypto Holdings
When planning to hold cryptocurrency for the long term, choosing a secure storage method is vital. Online wallets, while convenient, are more vulnerable to hacks. For enhanced security, cold storage options like hardware wallets are highly recommended. This section will discuss how cold storage protects your assets and how to create secure wallet backups.
Cold Storage and Hardware Wallets
Cold storage, particularly hardware wallets, provides the safest solution for long-term cryptocurrency storage. These physical devices store private keys offline, which makes them immune to online attacks such as hacking and phishing. Popular hardware wallets, like Ledger Nano X and Trezor Model T, are recommended for their security and ease of use.
Hardware wallets are like USB drives. They are portable. They let you manage your assets securely, offline. This makes them ideal for investors looking to hold large amounts of cryptocurrency over a long period. However, buy these wallets only from the manufacturer. This avoids tampered devices. Also, hardware wallets are very secure. But, users must protect their recovery phrases. Losing them can result in a permanent loss of assets.
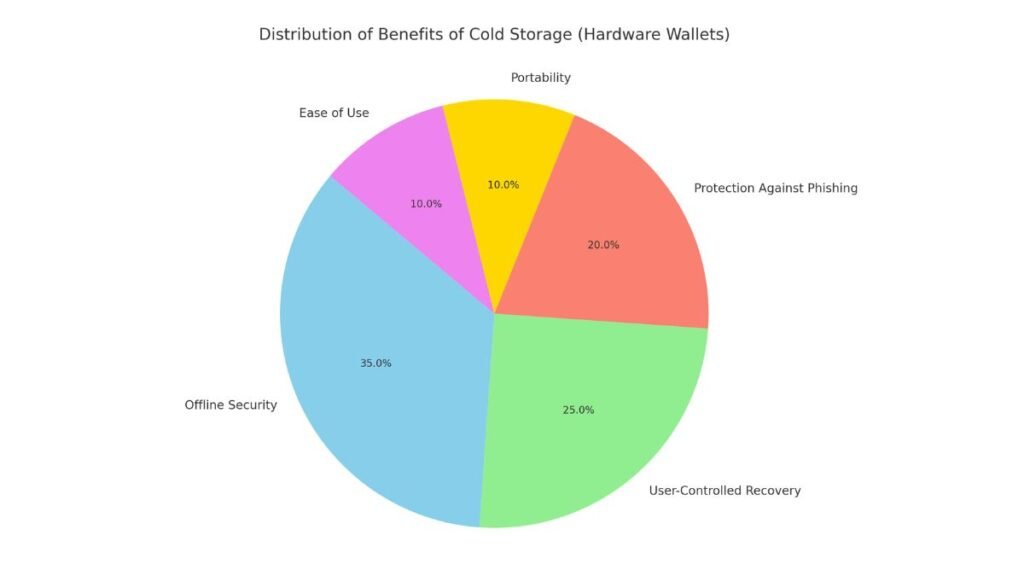
This pie chart shows the benefits of cold storage, especially hardware wallets. The chart highlights:
- Offline Security as the most significant benefit, contributing the most towards overall safety.
- User-Controlled Recovery and Protection Against Phishing are also substantial benefits.
- Portability and Ease of Use are represented, but are relatively smaller in importance compared to security aspects.
Creating Secure Wallet Backups
Backing up your wallet is just as important as choosing the right storage solution. It ensures that if your hardware wallet is lost, damaged, or stolen, you can still access your cryptocurrency. Secure backups involve multiple steps:
- Store Backup Files Offline: Use encrypted USB drives or external hard drives to store backups. These devices should be kept in safe, waterproof, and fireproof locations to avoid physical damage.
- Use Encrypted Devices: Encrypt your backups to prevent unauthorized access. For extra security, consider using Shamir Secret Sharing. It’s supported by wallets like Cypherock. It splits your backup into parts stored separately.
- Regular Updates: It’s important to regularly update your backups to reflect recent transactions. This ensures that your latest transactions are not lost if you need to restore your wallet.
Creating and managing backups is an ongoing process. Ensure they are stored in multiple secure locations and regularly check that they are updated and accessible.
Safeguarding Crypto Transactions
Performing cryptocurrency transactions involves certain risks, especially when you’re using unsecured networks. To ensure that your assets are protected, it’s essential to adopt strong security practices. Use only trusted, private networks. Consider using a VPN to secure your connections. Avoid public Wi-Fi. Use a VPN to prevent unauthorized access during transactions.
Using VPNs for Secure Transactions
A VPN is a great tool for protecting your crypto transactions. VPNs create an encrypted tunnel between your device and the internet, ensuring that no one can intercept your data. This is crucial when accessing exchanges or trading over public networks, like at cafes or airports. A VPN also masks your IP address, further enhancing your privacy and reducing the risk of being tracked by hackers or malicious actors.
Popular VPNs like NordVPN and ExpressVPN have strong security. They use AES-256 encryption, kill switches, and DNS leak protection. Some VPNs offer a Double VPN feature. It routes your data through two servers for extra security. Also, many VPNs now accept cryptocurrency for payment. This can further protect your anonymity.
Avoiding Public Wi-Fi for Crypto Transactions
Performing cryptocurrency transactions over public Wi-Fi is highly risky. Public networks are vulnerable to attacks like man-in-the-middle (MITM) attacks. Hackers can intercept your internet traffic. They can access sensitive info, like logins and private keys. Even seemingly secure networks, such as those in cafes or libraries, can be compromised.
To protect yourself, always avoid using public Wi-Fi when accessing your crypto wallets or exchanges. Instead, use a secure, private network, or switch to mobile data if necessary. If you must use public Wi-Fi, a VPN can offer protection by encrypting your connection and hiding your IP address. However, it’s safer to use private networks for sensitive financial transactions. For Safe Transactions:
- Avoid public Wi-Fi for all crypto transactions.
- Use a VPN for an encrypted and secure connection.
- Enable two-factor authentication (2FA) for extra security.
- Regularly update your wallet and VPN software to protect against vulnerabilities.
Related Topics:
- Setting up a crypto wallet
- Using Cryptocurrencies Securely
- Benefits of cold storage
- Protecting Your Crypto Assets
- pular crypto exchanges 2024
Securing your cryptocurrency is an ongoing task. It needs careful attention to best practices. Using cold storage, secure backups, and VPNs can greatly reduce the risk of theft and hacking. For long-term holdings, hardware wallets and vigilant network security are essential. Your awareness and actions will decide your investment’s safety in the fast-changing crypto space.



















