Understanding common crypto terms is essential for navigating decentralized finance (DeFi). These terms are the basics of cryptocurrency. They cover blockchain, crypto wallets, and smart contracts. As DeFi grows, knowing these terms will help you. It will let you make informed decisions and join the ecosystem with confidence. Today’s DeFi landscape introduces exciting opportunities, but with it comes new jargon. This guide simplifies complex crypto concepts, such as blockchain and wallets.
Understanding Blockchain and Cryptography
Blockchain technology and cryptography form the foundation of the entire cryptocurrency ecosystem. They ensure that every transaction within the network is secure, transparent, and tamper-proof. To navigate DeFi and cryptocurrencies, you must understand how these two technologies work.
What is Blockchain Technology?
At its core, blockchain is a decentralized digital ledger that stores transaction data across a network of computers or “nodes.” Unlike traditional databases that store data centrally, blockchain links transaction records (called “blocks“) into a chain. Each block has a unique hash of the previous block, ensuring data integrity and preventing tampering. This makes blockchain immutable—it cannot be changed or deleted once data is added.
Blockchain’s decentralized nature also makes it highly transparent. Anyone can view the transactions, although they cannot change or manipulate the data. This transparency is vital for trust in decentralized systems, especially in crypto.
How Cryptography Secures Transactions
Cryptography is the backbone of security in blockchain technology. It uses complex math to protect data and ensure only authorized users can access or modify it. Two key cryptographic techniques used in blockchain are hash functions and digital signatures.
- Hash Functions:
These generate a unique “fingerprint” (or hash) for each transaction based on the input data. Even the slightest change to the input data will produce a completely different hash, making it easy to detect any attempts at tampering. Hash functions are critical. They create new blocks and verify transactions in the blockchain.
- Digital Signatures:
Digital signatures verify the authenticity of transactions. Users sign a transaction with their private key when they initiate it. The network uses the corresponding public key to verify the signature is valid, ensuring that the transaction was authorized and has not been altered. This system ensures both confidentiality and integrity within the blockchain.
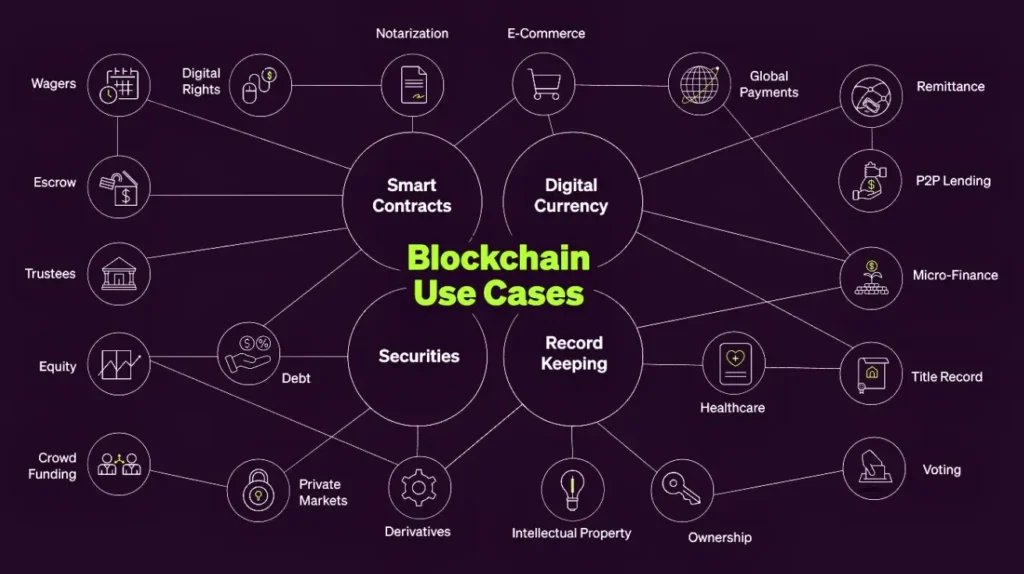
Understanding common crypto terms is crucial for anyone exploring the world of cryptocurrencies and decentralized finance (DeFi). As shown in the image, these terms cover foundational concepts like blockchain, wallets, and mining and more advanced ideas like smart contracts and liquidity pools. Mastering this vocabulary helps users confidently navigate the often complex crypto landscape, enabling them to participate in transactions, investments, and decentralized applications more effectively. Familiarizing yourself with these terms is the first step toward engaging with the digital economy.

Crypto Wallets and Keys: Storing Your Digital Assets
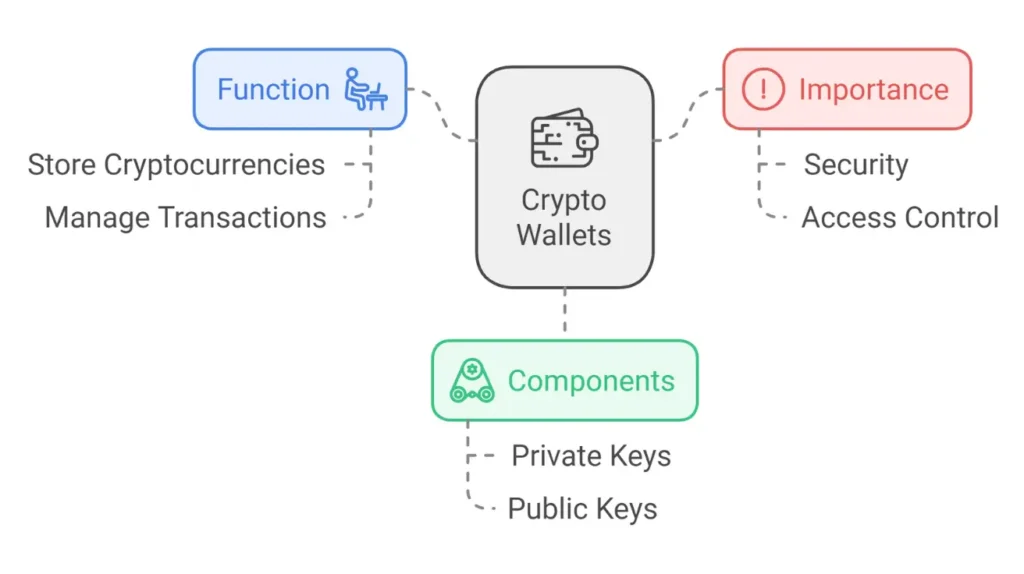
A crypto wallet is a critical tool for anyone managing cryptocurrencies. It functions as more than just a storage device—it safeguards the private keys that allow access to your digital assets. Without these keys, your assets are lost forever. So, crypto beginners must understand wallets and keys.
What is a Cryptocurrency Wallet?
A cryptocurrency wallet is a software or hardware that manages digital assets by storing public and private keys. These wallets don’t store cryptocurrency; they store the keys to access digital currencies on the blockchain.
There are several types of crypto wallets, each with unique benefits, Explained Difference Between Crypto Wallets in the following:
- Hardware Wallets:
These are physical devices, like USB drives. They store private keys offline, making them very secure against online threats. Popular hardware wallets include the Ledger Nano X and Trezor Model T, ideal for long-term storage of large amounts of cryptocurrency.

- Software Wallets:
You can install these applications on your desktop or mobile phone or access them via the web. They provide greater convenience for day-to-day transactions. However, because they are connected to the Internet, they are more vulnerable to cyberattacks.
- Paper Wallets:
Involve printing your public and private keys on paper. While secure from online hacks, the physical nature of paper wallets means they can be lost or damaged easily.
| Wallet Type | Security | Ease of Use | Best For |
|---|---|---|---|
| Hardware Wallet | High (Offline) | Less convenient | Long-term storage |
| Software Wallet | Moderate (Online) | Highly convenient | Daily transactions |
| Paper Wallet | High (Offline) | Inconvenient | Cold storage |
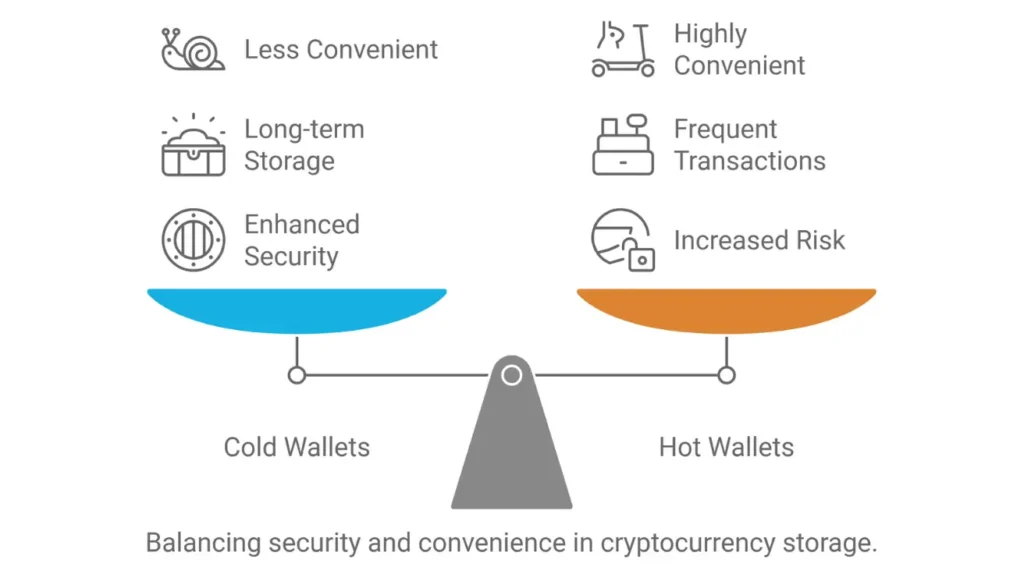
To clarify, we find two main types: cold storage (cold wallets) and hot storage (hot wallets). The key difference between these two methods lies in their accessibility and security. While cold wallets offer robust security by being offline, hot wallets provide easy access for frequent transactions through online connections.
- Cold Wallets
Cold wallets crypto, also known as offline wallets, store cryptocurrencies in devices not connected to the internet, such as USB drives or hardware devices. This method ensures enhanced security, making cold wallets ideal for the long-term storage of significant assets. However, using a cold wallet for everyday transactions is less convenient since you need to connect the device to the internet to transfer funds. Cold wallets are less susceptible to hacks, making them a preferred choice for those prioritizing security over convenience.
- Hot Wallets
By contrast, hot wallets are software-based wallets connected to the internet. They allow users to send and receive cryptocurrency quickly, making frequent transactions or daily use convenient. However, this convenience increases risk, as they are more vulnerable to hacking and online threats. Hot wallets are generally used for smaller amounts of crypto you plan to access regularly.
Note
Cold wallets are best suited for secure, long-term storage, while hot wallets are practical for regular, smaller transactions but come with higher security risks.
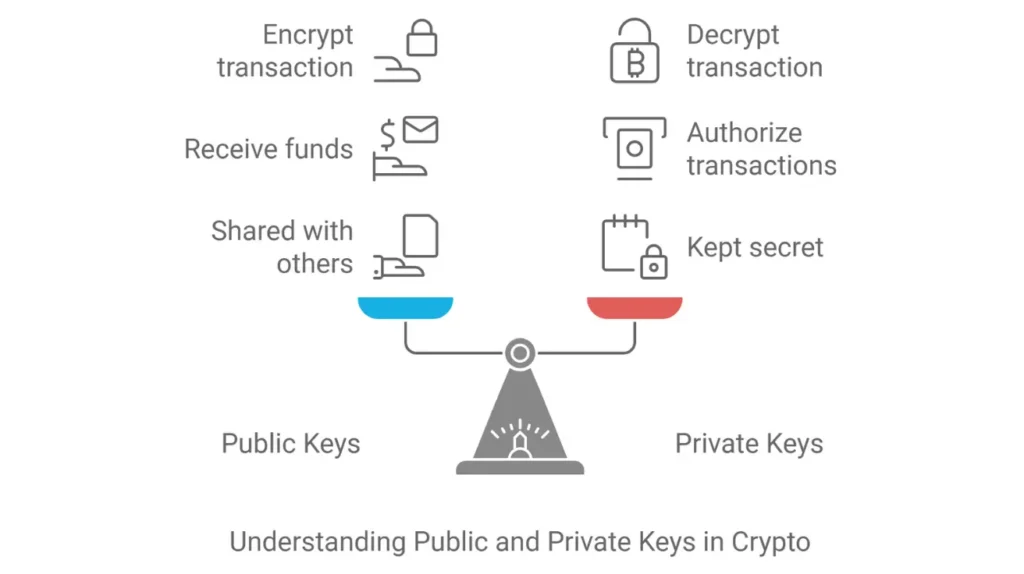
Public vs Private Keys in Crypto
In cryptocurrency, public and private keys are essential for securing assets. The public key is like your bank account number—you share it with others to receive funds. On the other hand, the private key is like your PIN—it’s secret, gives you access to your funds, and authorizes transactions.
When you make a transaction, the sender uses your public key to encrypt the transaction details, and you use your private key to decrypt them. This ensures that only you can access the funds or complete the transaction. You risk losing access to your assets without properly managing your private key.
Mining and Consensus Mechanisms
Mining and consensus mechanisms like Proof of Work (PoW) and Proof of Stake (PoS) are the engines that drive blockchain networks. These systems ensure that transactions are verified and recorded securely while maintaining decentralization. Understanding these processes is key to grasping how blockchain technology achieves trustless security.
What is the Bitcoin Mining Process?
The Bitcoin mining is integral to the Proof of Work (PoW) consensus mechanism. Miners compete to solve complex math puzzles. They validate transactions and create new blocks on the blockchain. The puzzle’s complexity adjusts based on the network’s total mining power, ensuring new blocks are added steadily. This energy-intensive process requires specialized hardware, such as ASICs (Application-Specific Integrated Circuits), to handle the necessary computations.
Miners earn newly minted Bitcoin and transaction fees for their work. This incentivizes them to keep securing the network. This process confirms transactions and ensures the blockchain remains resistant to tampering and fraud.
Proof of Work vs Proof of Stake
Bitcoin uses Proof of Work (PoW), which requires miners to expend significant computational power to solve puzzles. It is secure but energy-intensive and often criticized for its environmental impact. The more computational power a miner has, the higher their chance of validating the next block.
On the other hand, Proof of Stake (PoS) replaces miners with validators. They are chosen to create new blocks based on how much cryptocurrency they hold and “stake” as collateral. PoS significantly reduces energy consumption and can process transactions faster than PoW. Critics argue it may lead to centralization. Wealthy participants with more tokens would then control the network.
Note
Both systems have strengths. PoW is secure but resource-heavy. PoS is energy-efficient but may centralize power with large stakeholders.
Proof of Work (PoW) and Proof of Stake (PoS):
| Feature | Proof of Work (PoW) | Proof of Stake (PoS) |
|---|---|---|
| Energy Use | High | Low |
| Security | Strong, resource-intensive | Secure, risk of wealth centralization |
| Rewards | Mining rewards + fees | Staking rewards + fees |
| Speed | Slower, due to mining | Faster, with more scalability |
| Environmental Impact | Significant | Minimal |
Smart Contracts and Decentralized Applications (dApps)
Smart contracts and dApps are reshaping blockchain. They cut out middlemen and automate processes. Both are key to many blockchain projects, especially DeFi, providing more security and transparency.
What Are Smart Contracts?
Smart contracts are self-executing contracts whose terms are in code on a blockchain. When specific conditions are met, the contract runs the actions without a middleman. A smart contract can automate financial transactions, making them transparent, secure, and trustless. This removes the risk of manipulation or fraud, as all parties can verify the contract’s conditions.
Note
Smart contracts are widely used in DeFi projects, from decentralized exchanges to lending platforms. Their ability to enforce rules automatically makes them a powerful tool for developing trustless, efficient systems.
How dApps Work on Blockchain Networks
Decentralized applications (dApps) are blockchain-based software that operate without a central server. Unlike traditional applications (Apps). dApps run on peer-to-peer networks, using smart contracts as their back-end to execute specific actions when triggered by users. This makes dApps more secure, transparent, and resistant to censorship.
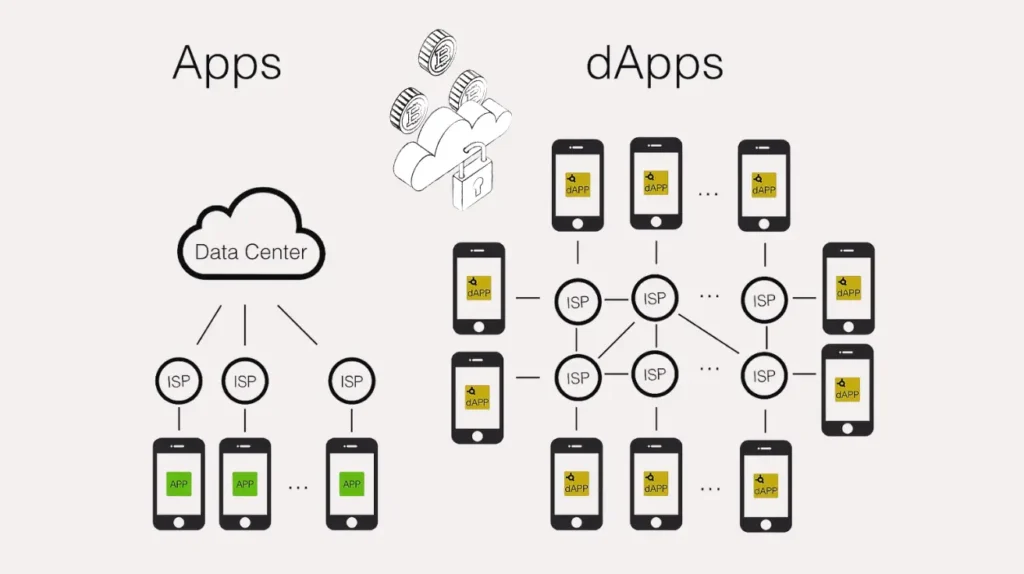
DApps can serve various purposes, such as financial services, gaming, and social networks. DeFi dApps like Uniswap and Aave let users trade or lend assets. They don’t rely on banks or other intermediaries. Their open-source nature enables innovation and collaboration within the blockchain community.
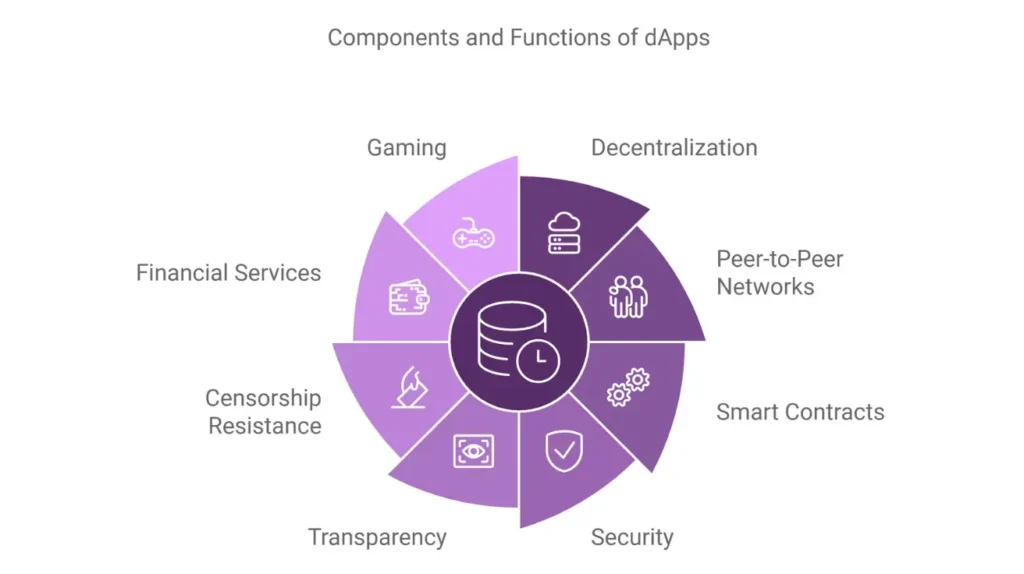
Common Crypto Terms in Decentralized Finance (DeFi)
Decentralized Finance (DeFi) lets users access financial services. These include lending, borrowing, and trading. It does this without using banks or middlemen. This peer-to-peer system uses blockchain and smart contracts. It creates trustless environments where users have full control of their assets. It’s crucial to know key DeFi terms. They will help you confidently use its various protocols and platforms.
What is Decentralized Finance (DeFi)?
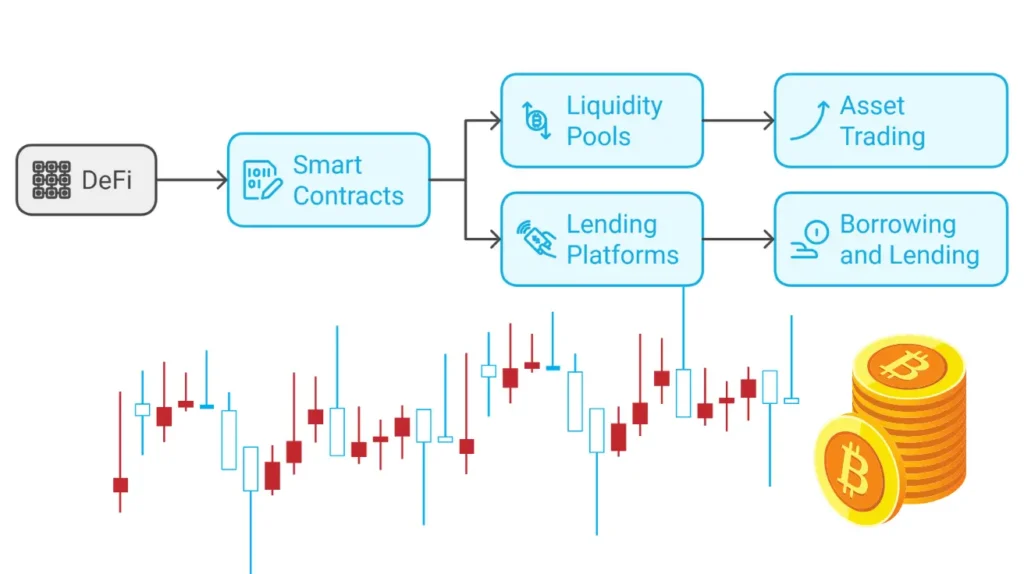
Decentralized Finance (DeFi) is a set of financial services. They run on blockchain networks, mainly Ethereum. Unlike traditional finance, DeFi operates without intermediaries such as banks. Instead, it uses smart contracts to automate financial transactions like lending and trading.
This boosts transparency and reduces the need to trust the other party. Core features include liquidity pools and lending platforms. Liquidity pools let users trade assets without a central order book, and lending platforms let users borrow or lend crypto. It changes finance by making services available to anyone with the internet.
Staking and Yield Farming
In staking, users lock up their cryptocurrency in a blockchain network (such as Ethereum or Solana) to support its operations. In return, they earn rewards in the form of more tokens. Staking is key to Proof of Stake (PoS) blockchains, in which validators verify transactions based on staked tokens.
Yield farming, on the other hand, involves providing liquidity to DeFi platforms in exchange for rewards. Yield farmers deposit pairs of tokens into liquidity pools on decentralized exchanges like Uniswap. In return, they earn a share of the trading fees generated from the pool. Yield farming usually offers higher returns but is riskier. It can cause impermanent loss, which happens when one token in a pair loses value compared to the other.
You Might Also Like:
- Blockchain Technology Explained
- What is Cryptocurrency
- Understanding Smart Contracts
- Choosing a Crypto Exchange
- Proof of Stake in Crypto
Decentralized Finance (DeFi) opens a new era of financial services. It is accessible and transparent. Users and Investors can lend, stake, and yield farms without intermediaries. By knowing terms like smart contracts, liquidity pools, and staking, users can navigate DeFi more confidently. However, with innovation comes risk, so staying informed and cautious is important. DeFi is a big shift toward more democratized finance. It brings both opportunities and challenges.



















